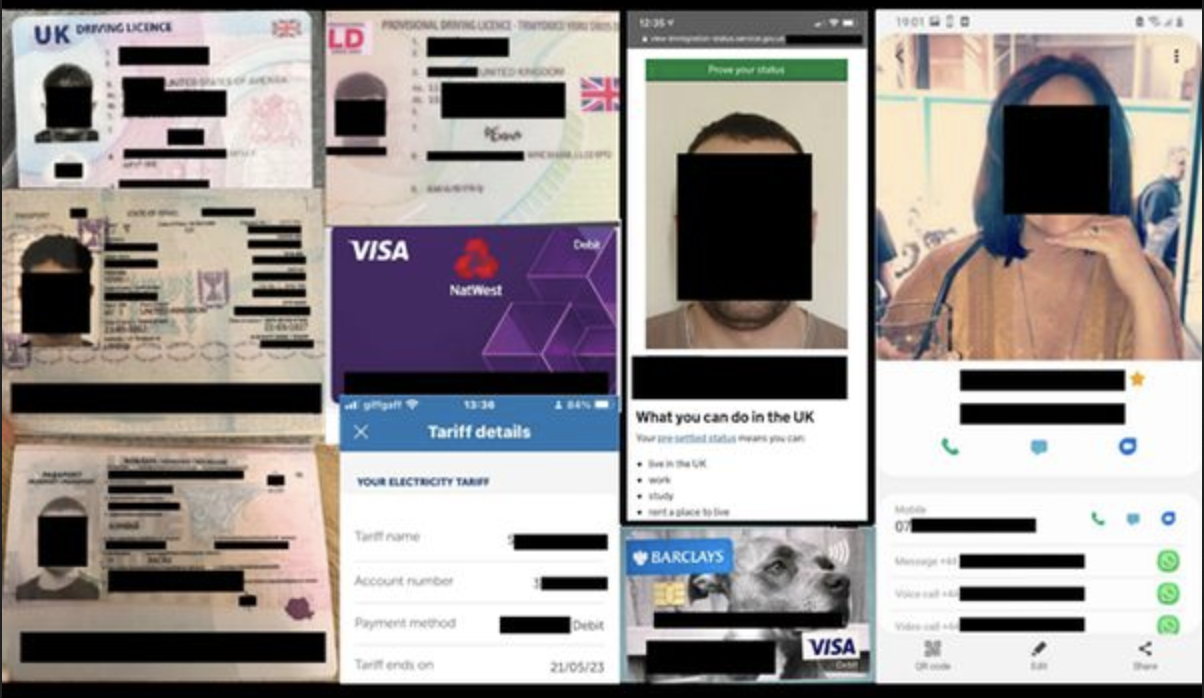
Massive Data Breach Exposes Sensitive Biometric Data and Personal Records
In a significant cybersecurity incident, a publicly exposed database has left 1,661,593 documents, totaling 496.4 GB, vulnerable to unauthorized access. This breach has compromised a wide range of sensitive information and documents, sparking serious concerns about privacy and security.
Breach Details
The exposed database contained highly sensitive biometric information, including facial scan images, fingerprints, signatures in both English and Hindi, and identifying marks such as tattoos and scars. It also included scans of critical personal documents such as birth certificates, testing and employment applications, diplomas, certifications, and other education-related files.
Particularly troubling were files that appeared to be verification documents containing the biometric data of police and military personnel. These records are crucial for identity verification and security, making their exposure especially concerning.
Investigative Findings
Further investigation revealed that the records belong to two separate entities: ThoughtGreen Technologies and Timing Technologies. These companies specialize in application development, analytics, development outsourcing, RFID technology, and biometric verification services. The shared nature of the records suggests that both companies operate under the same ownership or management, increasing the scope and severity of the breach.
Risks to Affected Individuals
The data breach affects a diverse group of individuals, including police officers, military personnel, and civilians. The exposure of biometric data poses significant risks:
- Identity Theft: Biometric data such as facial scans, fingerprints, and identifying marks are unique to each individual and cannot be changed. Once compromised, this information can be used for identity theft, potentially allowing unauthorized access to secure areas and systems.
- Unauthorized Access: With biometric data and personal documents exposed, malicious actors can potentially gain unauthorized access to secure facilities, systems, or personal accounts, putting individuals and organizations at risk.
- Fraud and Abuse: Exposed personal documents like birth certificates, employment applications, and diplomas can be used to create fake identities, leading to various forms of fraud and abuse.
What to Do When Biometric Data Is Exposed
For individuals affected by the exposure of their biometric data, immediate steps should be taken to mitigate potential risks:
- Monitor Financial Accounts: Keep a close watch on bank accounts, credit card statements, and credit reports for any suspicious activity. Report any unauthorized transactions immediately.
- Enhance Security Measures: Use multifactor authentication (MFA) where possible, combining biometric verification with other forms of authentication such as passwords or security tokens.
- Notify Relevant Authorities: Report the breach to relevant authorities and institutions. For police and military personnel, notify your superiors and follow any specific protocols for dealing with data breaches.
- Stay Informed: Keep abreast of any updates from ThoughtGreen Technologies and Timing Technologies regarding the breach and follow any recommended steps they provide.
- Consider Identity Theft Protection Services: Enroll in identity theft protection services that can monitor for misuse of your personal information and offer assistance in recovering from identity theft.
- Limit Use of Biometric Data: Where feasible, limit the use of biometric data for critical security processes and consider alternative forms of identification.
The ThoughtGreen Technologies and Timing Technologies data breach highlights the urgent need for robust cybersecurity measures, especially when dealing with sensitive biometric data and personal records. The incident involving ThoughtGreen Technologies and Timing Technologies serves as a stark reminder of the risks associated with inadequate data protection and the extensive consequences of such breaches. As investigations continue, it is essential for organizations worldwide to re-evaluate their security practices and ensure their data is protected against unauthorized access and cyber threats.

Our team of writers, armed with a healthy dose of caffeine and an overflowing imagination covers wacky and weird news. From politics to pop culture, from bizarre headlines to analysis, we take a sideways glance at the world’s happenings, delivering news in a way that’s informative, entertaining, and occasionally eyebrow-raising.